Table of Contents
- Understanding Phishing Attacks
- What is Email Phishing?
- Common Types of Phishing Scams: With Examples
- How can a Business Protect Against Phishing Attacks?
- Next Steps
E-mail threats continue to nip at businesses daily. Hackers hope to trap those users who are not trained on the phishing threats of today’s world by leading them to click on content they shouldn’t. Ultimately, the end user’s account is compromised and used to send out the same threat to others.
Email phishing is a cyber attack hackers use to trick business users into revealing sensitive information such as usernames, passwords, credit card numbers, personal data, etc. They do this by posing as legitimate and trustworthy e-mail senders. Often, the e-mails will appear to come from a well-known contact or company to gain the user’s trust. Today, more than ever, end user training should be the highest priority for businesses today.
Lets take a closer look on what phishing e-mails might contain:
Spoofed Sender Address
Often sender emails are manipulated to appear as if it’s coming from a reputable source even though it’s controlled by the attacker.
Many times, this could be a contact or business you have e-mailed in the past. The hacker will spoof their e-mail to look like theirs in hopes the end user falls for the trick.
An example of this would be a CEO or CFO of a company who works with suppliers in foreign countries may request wire transfers to the supplier be sent to a different payment method.
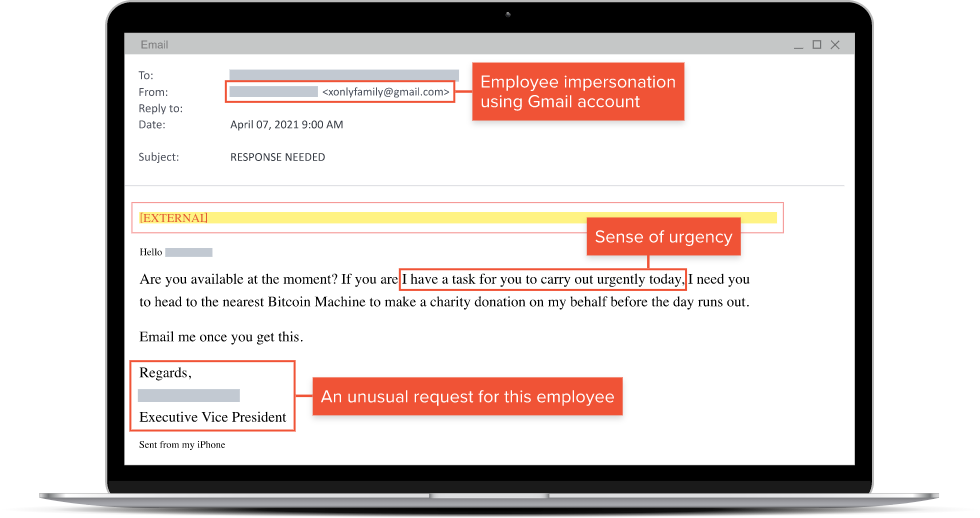
Urgent or Alarming Content
Phishing emails also provide the end user with a sense of urgency or panic. The hope is to pressure the user into taking immediate action without considering the legitimacy of the email or the consequences.
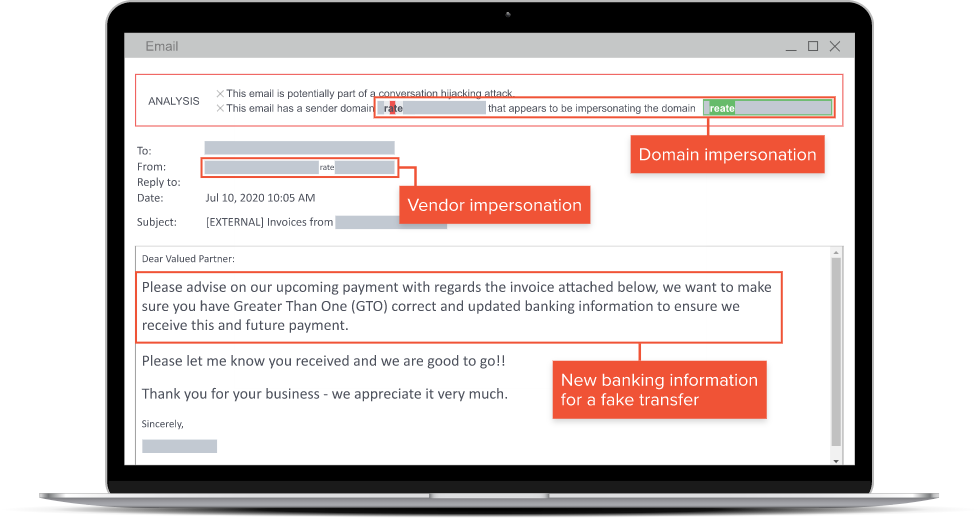
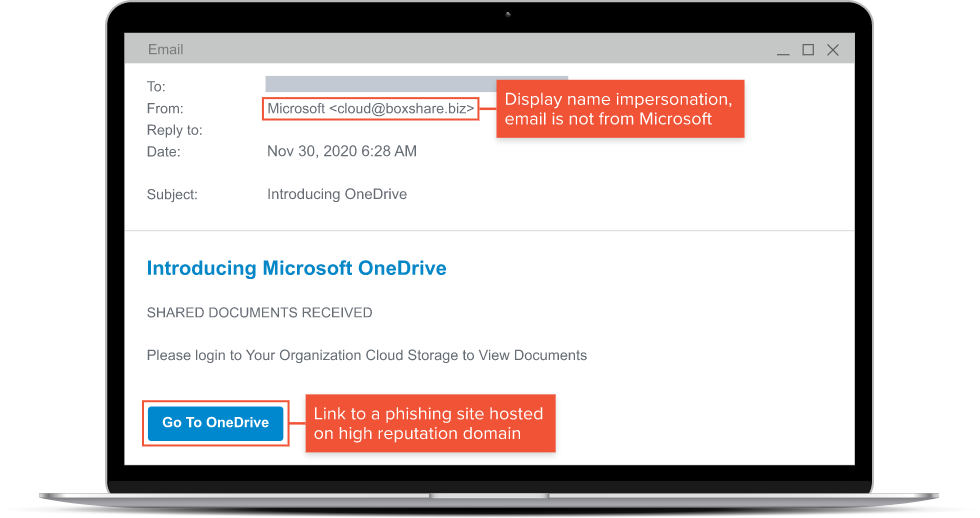
Deceptive Links
Emails may contain links that appear to be legitimate but redirect the user to a fake website designed to collect their information when they attempt to log in. This is often seen with emails that look like they are coming from Microsoft, the correct logos, color scheme, and terminology.
This is often seen when users have Microsoft 365 services, they receive e-mails that appear to come from the service, and voluntarily provide their information by clicking the deceptive links.
Malicious Attachments
Attachments often are tied to phishing e-mails that are meant to be harmful. They carry malware or viruses that infect the user’s computer who opened it. Linked to these types of cyber threats is ransomware which more often than none crawl out to businesses infrastructure to infect company data.
Social Engineer Tactics
Social engineering is a technique used by attackers to manipulate people into providing confidential or sensitive information which might compromise security.
It involves psychological approaches that exploit human emotions, trust, and behaviors to gain access to sensitive information. It can be used in various means including in-person interactions, phone calls, text messages, social media, and of course, phishing e-mails.
The goal of email phishing attack is to obtain sensitive information that an attacker can use for a variety of reasons; stealing money, identify theft, unauthorized access to company e-mails and data, compromising business users to use their e-mail to attack others, etc.
How can a business protect themselves?
There are several approaches that should be combined, to help protect the business and users from falling victim to email phishing. To protect yourself from email phishing the following should be considered:
Verify Sender Information
Users should always check sender’s email addresses carefully and be cautious of all emails. Especially those that are unfamiliar or suspicious addresses.
A good rule to follow is that if a user is not anticipating an e-mail with links or attachments from a sender to ignore it. Verify that it’s legit. Email the user on the side, call them directly, and confirm that the email is directly from them. Take the extra time now vs needing the extra time to recover.
Avoid Unknow Sender Links and Attachments
Don’t click on links, downloads, or attachments from unknown sources. Simply ignore them and trash them.
Same rule applies from above. If in doubt don’t engage with the e-mail and report it to your IT provider.
Don’t Provide Sensitive Information Over Email or Links to Suspicious Webpages
It’s uncommon for legitimate organizations and vendors to ask for sensitive information like passwords, credit card details, your 2FA temporary codes, etc.
Enable Two-Factor Authentication on Email Services
Commonly enough this is still a challenge for some businesses. Whenever possible enable 2FA on all user accounts that use email services. Take an extra step further and require them to use mobile app authenticator vs a text with a code. There has been a rise of compromises where users voluntarily enter their 2FA temporary code into a suspicious webpage providing full email access to the attackers.
This extra layer of security is a must to help protect a business from attackers and users from falling victim.
Email Spam Gateway and Antivirus
Every business should have a spam filter service in front of their e-mail services. Some of these services have additional tools that add more security to an environment as well as additional protection against attacks on their users. Additionally, having a good antivirus protection solution on user machines helps when users voluntarily engage in downloading and running malicious threats.
Train, Educate, and Repeat!
This is one of the most important takeaways. Train and educate. Always. Ongoing training should be part of the businesses plan. Threats change daily, new hires are brought in monthly, and to stay on top of these threats it must be a continuous effort.
Phishing training and campaigns to users on a regular basis will help increase a business’s chance of not falling victim to these threats.
A business must be vigilant, cautious, and disciplined when dealing with emails. It will significantly reduce the risk of falling victim to phishing attacks.
Next Steps
Email threats come in many forms and can cause significant harm to both individuals and organizations. Be vigilant and aware of these threats and take the necessary steps to protect yourself. Contact Advance2000 today if you need to protect your email and offer phishing training. We have solutions that reduce business risk by making your email safe and more secure.



